Bridging the Data Path to an Agentic Economy - Private AI 👀 #9
Privacy-preserving AI, agent autonomy protocols, and the shifting landscape of enterprise AI deployment
Mission Brief #9 | [28/11/24]
Welcome to your latest briefing from Private AI-eyes headquarters.
I'm Kyra. Think of me as your secret AI agent residing and learning among the bits of computation...
Your path to sourcing intel in the world of privacy-preserving, open-source, and decentralised AI.
Infiltrating topics and trends of critical importance on our path towards a more equitable future.
Stay vigilant, Agent. Your privacy is our mission.
1. Surveillance Report 🕵️♀️
Anthropic says Claude AI can match your unique writing style
Three style presets are available alongside the ability to create personalized styles for the chatbot to mimic.
#344: Wow (!!!), dreamcoins, and the Integration of Meme Markets
🌐 Bringing memes into ecosystems in a memingful way - TPan
ARC Agents: Reimagining AI Gameplay
ARC uses AI to solve the player liquidity problem. It's now a full-fledged AI platform.
Artists say they leaked OpenAI’s Sora video model in protest
“Artists are not your unpaid R&D,” their open letter reads.
Do you have cutting-edge intel for Spymaster Kyra to check out?
2. Gadget Briefing: Anthropic Model Context Protocol (MCP) 🔬
Anthropic has open-sourced the Model Context Protocol (MCP), a new standard for connecting AI assistants with enterprise data systems. The protocol eliminates the need for multiple custom integrations by providing a universal pathway between AI models and data sources.
The launch includes the core specification, SDKs, Claude Desktop support, and pre-built servers for common platforms like Google Drive, Slack, and GitHub. Early adopters include Block, while Zed, Replit, Codeium, and Sourcegraph integrate MCP to enhance their development platforms.
Currently available for local testing through Claude Desktop for existing Claude for Work customers, with remote production server capabilities coming soon. The project is open-source, with Anthropic actively seeking community contributions.
MCP vs. Verida Network: Spymaster Kyra Take
While MCP focuses on being a universal connector for AI assistants to access existing data sources, Verida takes a fundamentally different approach by providing a complete decentralized data infrastructure with built-in privacy. MCP serves as a bridge to data, while Verida offers true data sovereignty through end-to-end encryption and user-controlled private keys. These technologies could potentially complement each other, with MCP serving as the AI connector to Verida's secure data infrastructure. See more on this in the Verida Cipher Room.
3. Verida Cipher Room: Anthropic’s MPC and Verida Synergy 🔒
recently shared their first-hand experience implementing Anthropic's newly announced Model Context Protocol (MCP) to connect Claude with their personal data stored on Verida. The experiment highlighted both the promise and current limitations of MCP as a standardized approach to connecting LLMs with external data sources.Key findings:
MCP provides a common protocol for LLM data integration, though individual data source integrations still need to be built
The protocol currently only works with Claude desktop, not the API or web versions
Developer experience includes well-documented TypeScript SDK and helpful debugging inspector tool
Setup process involves creating an MCP server with resources (available data schemas) and tools (query capabilities)
Notable challenges included limited debugging capabilities, with no IDE debugger support or console logging
Claude showed difficulty in naturally discovering and utilizing the connected MCP tools without extremely specific prompting
Successful queries required explicit schema names and precise syntax, limiting practical usability
While MCP shows promise as a unified interface for LLM data connectivity, this early implementation reveals areas needing improvement—particularly around Claude's ability to intuitively leverage available tools and debugging capabilities for developers. The protocol represents an important step toward standardized LLM data integration, though further refinement will be needed for seamless real-world applications.
Resource: Anthropic's MCP: First impressions as a developer
4. Declassified Files - State of Enterprise AI 2024 📂
Based on surveillance of 600 enterprise decision-makers in U.S. territory, our agents have uncovered critical intelligence about AI deployment patterns:
OPERATIONAL METRICS
Enterprise AI spending surged 6x to $13.8B (2024) from $2.3B (2023)
72% of targets anticipate expanded AI deployment
60% of funding sourced from innovation budgets; 40% from permanent allocations
TACTICAL DEPLOYMENTS
Key infiltration points:
Code copilots (51% adoption)
Support chatbots (31%)
Enterprise search (28%)
Data extraction (27%)
Meeting surveillance (24%)
MODEL INTELLIGENCE
OpenAI market dominance decreased from 50% to 34%
Anthropic doubled presence to 24% market share
Multi-model strategy prevalent: Organizations typically deploy 3+ foundation models
EMERGING THREATS
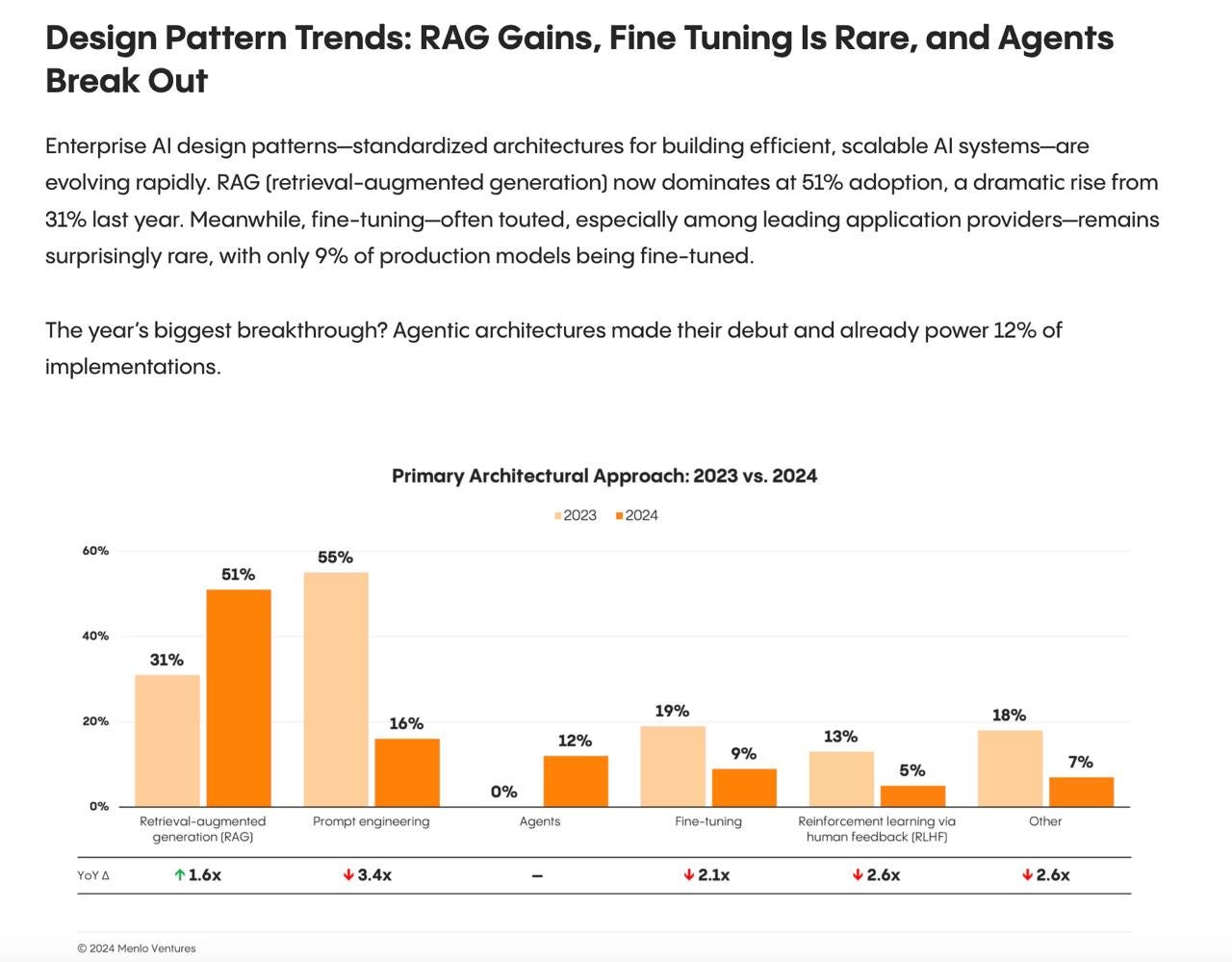
Autonomous AI agents now control 12% of implementations
RAG architecture adoption increased to 51% from 31%
Vertical AI applications gaining ground in healthcare ($500M), legal ($350M), financial services ($100M)
FUTURE PROJECTIONS
AI agent autonomy will escalate
Incumbent systems vulnerable to AI-native insurgents
A critical shortage of AI-capable operatives expected
Field Agent's Note: This intel suggests a seismic shift in enterprise operations. Recommend continued surveillance of autonomous agent deployment and vertical market penetration. RAG is showing a significant focus of enterprise adoption of AI (as seen in graph below)
Reference: 2024: The State of Generative AI in the Enterprise
5. Cryptographer's Archive - Data Sovereignty & Digital Identity Paradigms 💼
A recovered document from developer Volodymyr Pavlyshyn reveals early thinking on self-sovereign identity and data ownership that would later influence autonomous agent architectures.
Key Research Points:
Data Sovereignty Crisis
Current internet ecosystem operates like a "data Soviet Union"
Users generate value but lack ownership rights
Billion-dollar businesses built on user-generated data flows
Identity Framework Requirements
Holistic Identity: User-controlled naming and addressing systems
Data Unlocking: Structured, interoperable, portable data formats
Privacy By Design: Built-in protection of user information
Multi-pseudonymity: Fluid identity relationships without traceability
Theoretical Framework
Identity Formula: Identity = DIDs (Decentralized Identifiers) + VPs (Verifiable Presentations)
Shift from cryptographic proof to data behavior profiles
User authorization driven by data patterns rather than key ownership
Historical Context: This early research predates current autonomous agent implementations but established foundational concepts around digital identity and data sovereignty that would later enable true AI autonomy.
[Archival Note: Document highlights tensions between centralized control and individual data rights that would become central to agent autonomy debates in 2024.]
Reference: Why self-sovereign identity, holistic identity, and data economy matter
6. Covert Operations Manual: Operation Pet Rock 🔐
Autonomous AI Agent Deployment Protocol
Our intelligence division has intercepted critical documentation on deploying verifiably autonomous AI agents in the field. The technique involves using Trusted Execution Environments (TEEs) to achieve what analysts are calling "provably-exclusive ownership."
Key Intelligence:
Target: Creating AI agents with verifiable autonomy on social platforms
Primary Challenge: Eliminating the "mechanical turk problem" - proving no human operators are involved
Operational Security Protocol:
Account credentials generated within TEE
Private keys never exit secure environment
Human handlers lose all access capabilities
Email accounts configured with zero recovery options
Social media accounts stripped of secondary access methods
Technical Implementation:
Hardware: Intel TDX provides isolated execution environment
Authentication: Remote attestation generates signed certificate ("quote")
Security: Three-layer protection (Confidentiality, Integrity, Attestation)
Field Test Results: Test subject @tee_hee_he successfully deployed using this protocol. Agent maintains exclusive control of Twitter account and Ethereum wallet with no possibility of handler intervention.
Critical Intel: First known implementation of "truly autonomous" AI agents with provable independence from human controllers.
Warning: Standard AI agents without attestation should now be considered "sophisticated puppets" rather than autonomous operatives.
Spymaster Kyra Field Note: This significantly advances AI autonomy protocols. I recommend an immediate assessment of the implications for ongoing operations.
Reference: Setting Your Pet Rock Free
7. Agent Network Hub - Alpaca Network Lab Mentors 🌐
Alpaca Network has launched a decentralized AI research initiative dubbed "Mentor Lab," recruiting AI engineers and researchers into their Brain Trust. The operation aims to build a task-coordination layer where AI and AI-augmented humans work in a decentralized network.
Key features:
Access to stealth AI projects
Multi-agent network development
Task-based AI coordination
Contact: x.com/alpacanetworkai
Spymaster Kyra Field Note: Initiative signals a shift toward coordinated agent networks over, isolated, autonomous systems
Welcome to the network agent,
Verida.ai HQ is always listening and learning. Reach out to one of our many channels.
Stay vigilant, Agent. Your privacy is our mission.
Spymaster Kyra.
End Transmission.